In the rapidly evolving digital era, AWS IoT Remote Access has emerged as a groundbreaking solution for businesses aiming to enhance connectivity and simplify device management. This advanced technology allows secure and effortless access to IoT devices from anywhere, transforming it into an indispensable tool for modern enterprises. By utilizing AWS IoT Remote Access, organizations can unlock new opportunities for remote monitoring, diagnostics, and troubleshooting, significantly boosting operational efficiency and fostering innovation.
AWS IoT Remote Access is not merely a technological advancement but represents a pivotal shift in how businesses interact with their IoT ecosystems. The capability to remotely access devices empowers companies to respond swiftly to challenges, minimize downtime, and improve overall productivity. As the Internet of Things continues to expand, the demand for robust remote access solutions such as AWS IoT Remote Access is set to rise exponentially.
With the increasing dependence on connected devices, ensuring secure and reliable remote access has become a top priority for organizations. AWS IoT Remote Access addresses this critical need by offering a scalable, secure, and user-friendly solution that integrates seamlessly with existing systems. This article explores the nuances of AWS IoT Remote Access, examining its features, benefits, applications, and best practices for successful implementation.
Read also:Can Hens Lay Eggs Without A Rooster Understanding The Science Behind Egg Production
Table of Contents
- Introduction to AWS IoT Remote Access
- Key Features of AWS IoT Remote Access
- How AWS IoT Remote Access Works
- Security Considerations in AWS IoT Remote Access
- Benefits of Using AWS IoT Remote Access
- Real-World Applications of AWS IoT Remote Access
- Steps for Implementing AWS IoT Remote Access
- Best Practices for AWS IoT Remote Access
- Challenges and Solutions in AWS IoT Remote Access
- Future Trends in IoT Remote Access
- Conclusion
Exploring AWS IoT Remote Access
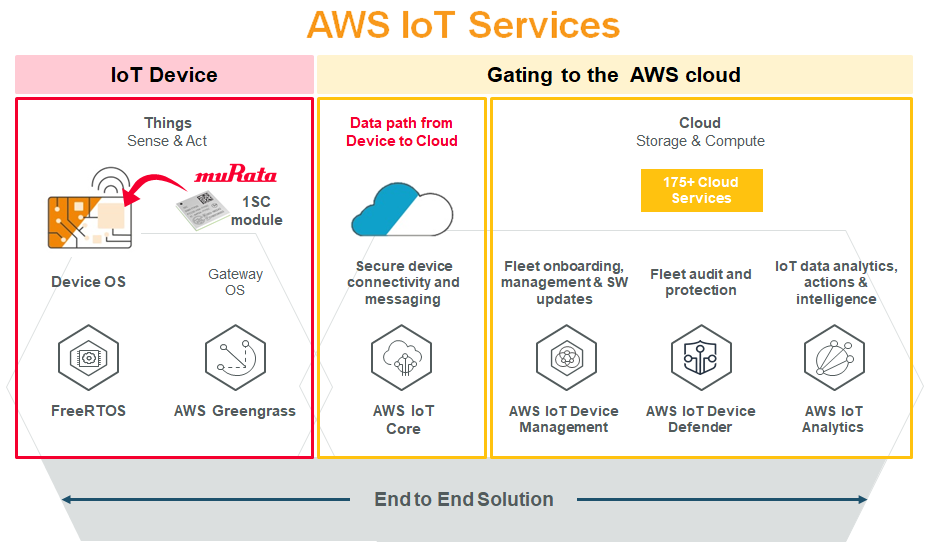
AWS IoT Remote Access is a cloud-based service meticulously designed to facilitate secure and efficient remote access to IoT devices. This service harnesses the immense power of AWS's extensive infrastructure to provide a scalable solution for managing and monitoring connected devices. By enabling remote access, AWS IoT Remote Access empowers businesses to perform crucial tasks such as diagnostics, firmware updates, and troubleshooting without the need for physical presence, streamlining operations and enhancing productivity.
Why AWS IoT Remote Access Stands Out
Among the myriad of remote access solutions available, AWS IoT Remote Access distinguishes itself through its seamless integration with the AWS ecosystem. This ensures perfect compatibility with other AWS services, including AWS IoT Core, AWS Lambda, and Amazon S3. Moreover, its robust security features and intuitive user interface make it an excellent choice for organizations of all sizes, from startups to global enterprises.
Here are some compelling reasons to choose AWS IoT Remote Access:
- Scalability: Manage thousands of devices effortlessly.
- Security: Advanced encryption and authentication protocols safeguard sensitive data.
- Integration: Works harmoniously with other AWS services for a cohesive experience.
- Cost-Effectiveness: Pay only for the resources you consume, optimizing budget allocation.
Comprehensive Features of AWS IoT Remote Access
AWS IoT Remote Access boasts a robust set of features tailored to meet the diverse needs of modern enterprises. These features are meticulously crafted to enhance the functionality and usability of the service, ensuring a seamless and efficient remote access experience for users.
1. Secure Tunneling
Secure tunneling forms the backbone of AWS IoT Remote Access. This feature enables encrypted communication between devices and applications, ensuring that sensitive data remains secure during transmission. It is particularly beneficial for industries like healthcare and finance, where data security is paramount and compliance with stringent regulations is non-negotiable.
2. Device Authentication
Device authentication is a critical component of AWS IoT Remote Access, ensuring that only authorized devices can connect to the service. This is achieved through the use of X.509 certificates and AWS IoT Device Defender, which continuously monitor device behavior and promptly detect any anomalies, enhancing overall security.
Read also:How To Effectively Remove Lip Balm Stains From Clothes
3. Scalability
Built on AWS's scalable infrastructure, AWS IoT Remote Access is equipped to handle vast volumes of devices and data. This makes it an ideal solution for both small-scale projects and enterprise-level deployments, accommodating the growing demands of expanding IoT ecosystems.
Understanding the Mechanics of AWS IoT Remote Access
To effectively implement AWS IoT Remote Access, it is essential to comprehend its underlying mechanisms. At its core, the service operates by establishing secure tunnels between devices and applications. These tunnels facilitate encrypted communication, ensuring that data remains secure during transmission.
Steps in Establishing a Secure Tunnel
Here is a detailed breakdown of how AWS IoT Remote Access establishes a secure tunnel:
- The client application initiates a request to AWS IoT Remote Access, marking the beginning of the connection process.
- AWS IoT Remote Access verifies the client's identity and establishes a secure connection, ensuring that only authorized entities gain access.
- A secure tunnel is created between the client and the target device, providing a dedicated pathway for data transmission.
- Data is transmitted securely through the tunnel, maintaining confidentiality and integrity throughout the process.
Security Priorities in AWS IoT Remote Access
In the realm of IoT remote access, security remains a top concern. AWS IoT Remote Access employs a multi-layered security approach, combining encryption, authentication, and authorization mechanisms to safeguard sensitive information at all times.
Best Security Practices
To maximize the security of AWS IoT Remote Access, organizations should adhere to the following best practices:
- Strong Authentication: Utilize strong passwords and multi-factor authentication to protect access points.
- Regular Updates: Keep firmware and software on devices up to date to mitigate vulnerabilities and protect against emerging threats.
- Behavior Monitoring: Continuously monitor device behavior for any suspicious activity using AWS IoT Device Defender.
- Access Control: Restrict access to authorized personnel only, ensuring that sensitive data remains protected.
Advantages of Utilizing AWS IoT Remote Access
The benefits of AWS IoT Remote Access extend far beyond its core remote access capabilities. This service offers a multitude of advantages that can significantly enhance business operations and drive innovation. Below are some key benefits:
1. Enhanced Operational Efficiency
By enabling remote access, AWS IoT Remote Access drastically reduces the need for on-site visits, saving valuable time and resources. This leads to increased operational efficiency and improved productivity, allowing businesses to focus on strategic initiatives.
2. Superior Security
With its cutting-edge security features, AWS IoT Remote Access ensures that sensitive data remains protected, minimizing the risk of breaches and unauthorized access. This fosters trust and confidence among stakeholders.
3. Scalability
As businesses grow, so do their IoT ecosystems. AWS IoT Remote Access provides the scalability required to accommodate this growth, ensuring that organizations can efficiently manage increasing numbers of devices and data.
Practical Applications of AWS IoT Remote Access
AWS IoT Remote Access finds application across a wide array of industries, transforming the way businesses interact with their IoT devices. Below are some real-world examples illustrating its diverse applications:
1. Manufacturing
In the manufacturing sector, AWS IoT Remote Access is leveraged for remote monitoring and diagnostics of machinery. This empowers engineers to promptly identify and resolve issues, minimizing downtime and optimizing production efficiency.
2. Healthcare
In healthcare, AWS IoT Remote Access facilitates the remote monitoring of medical devices, ensuring that patients receive timely and accurate care. It also enables healthcare providers to securely access patient data from anywhere, enhancing the overall quality of care.
Guidelines for Implementing AWS IoT Remote Access
Implementing AWS IoT Remote Access involves several critical steps that ensure a smooth and successful deployment of the service. Below is a comprehensive guide to implementing AWS IoT Remote Access:
Step 1: Configure AWS IoT Core
Begin by setting up AWS IoT Core, which serves as the foundation for AWS IoT Remote Access. This involves creating an AWS account and configuring the necessary settings to align with your organizational requirements.
Step 2: Register Devices
Register the devices you intend to connect to AWS IoT Remote Access. This process involves assigning unique identifiers and configuring security settings to ensure secure and reliable communication.
Step 3: Establish Secure Tunnels
Establish secure tunnels between devices and applications, ensuring that data is transmitted securely and maintaining the integrity of sensitive information.
Optimizing AWS IoT Remote Access
To fully leverage the potential of AWS IoT Remote Access, it is crucial to follow best practices. These practices ensure optimal performance, security, and reliability of the service. Below are some key best practices:
1. Regular Firmware Updates
Keeping device firmware up to date is vital for maintaining security and functionality. Regular updates safeguard devices against the latest threats and vulnerabilities, ensuring they operate at peak performance.
2. Continuous Device Monitoring
Monitoring device behavior helps detect anomalies and potential security threats. Use AWS IoT Device Defender to continuously monitor and analyze device activity, ensuring early detection and resolution of issues.
Addressing Challenges in AWS IoT Remote Access
While AWS IoT Remote Access offers numerous advantages, it also presents certain challenges. Below are some common challenges and their solutions:
1. Security Concerns
Security remains a significant concern in IoT remote access. To mitigate this, organizations should implement robust security measures, such as advanced encryption and multi-factor authentication, ensuring maximum protection of sensitive data.
2. Scalability Issues
As IoT ecosystems expand, scalability becomes a critical challenge. AWS IoT Remote Access addresses this by providing a scalable infrastructure capable of handling increasing numbers of devices and data, ensuring smooth operations even as the ecosystem grows.
Emerging Trends in IoT Remote Access
The future of IoT remote access is promising, with several trends shaping its evolution. Below are some key trends to watch:
1. Enhanced Security Measures
As cyber threats continue to evolve, so will security measures. Future IoT remote access solutions will likely incorporate advanced encryption and authentication protocols, ensuring maximum security and protecting against emerging threats.
2. Integration with Artificial Intelligence
The integration of AI with IoT remote access will enable smarter, more autonomous systems. This will enhance the capabilities of remote access solutions, making them more efficient, effective, and capable of addressing complex challenges.
Final Thoughts
AWS IoT Remote Access marks a significant leap forward in the realm of IoT remote access. By offering a secure, scalable, and user-friendly solution, it empowers businesses to unlock the full potential of their IoT ecosystems. Whether you're in manufacturing, healthcare, or any other industry, AWS IoT Remote Access provides the tools and features necessary to thrive in today's digital age.
We encourage you to delve deeper into AWS IoT Remote Access and consider implementing it within your organization. For more information, visit the official AWS website or consult an AWS representative. Share your thoughts and experiences in the comments section below, and explore our other articles for valuable insights into the world of IoT and cloud computing.