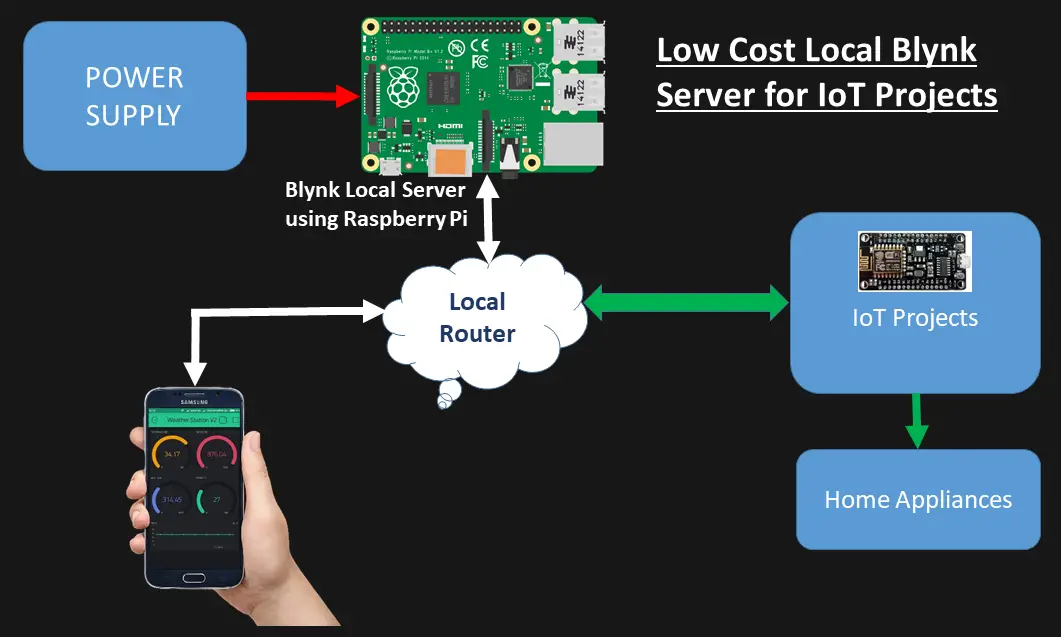
In today’s fast-paced digital era, integrating IoT SSH server technology has become essential for ensuring secure communication and efficient remote management of IoT devices. As more industries and individuals adopt IoT solutions, the demand for robust security measures has never been greater. This article delves into the world of IoT SSH servers, exploring their functionality, advantages, and best practices to help you unlock their full potential.
IoT SSH server technology provides a reliable framework for safeguarding data exchanges between interconnected devices. With the increasing prevalence of cyber threats, understanding how to implement secure communication protocols is crucial for both large-scale enterprise operations and personal projects. This guide aims to empower readers with the knowledge needed to deploy and manage IoT SSH servers effectively.
By the end of this article, you will have a thorough understanding of IoT SSH servers, their role in enhancing security, and practical strategies for implementation. Whether you’re a developer, IT professional, or simply someone interested in IoT security, this guide will offer valuable insights to help you make well-informed decisions.
Read also:Exploring Mannie Freshs Musical Legacy And Financial Success
Table of Contents
- What is an IoT SSH Server?
- Why SSH is Crucial for IoT
- Key Features of IoT SSH Servers
- Advantages of Using IoT SSH Servers
- How to Set Up an IoT SSH Server
- Security Best Practices for IoT SSH Servers
- Common Issues and Solutions
- Real-World Case Studies
- Emerging Trends in IoT SSH Technology
- Conclusion and Next Steps
What is an IoT SSH Server?
An IoT SSH server is a specialized platform designed to facilitate secure communication between IoT devices using the Secure Shell (SSH) protocol. SSH is a cryptographic network protocol that ensures secure data transmission, remote command execution, and file transfer across unsecured networks. In the realm of IoT, SSH servers play a vital role in maintaining the integrity and confidentiality of data exchanged between devices.
IoT SSH servers are indispensable for managing extensive IoT deployments where numerous devices require remote monitoring and control. By leveraging SSH, organizations can establish encrypted connections, authenticate devices, and execute commands securely, thereby minimizing the risk of unauthorized access or data breaches.
How IoT SSH Servers Operate
IoT SSH servers function by creating a secure channel between a client device and the server. This process involves several critical steps:
- Authentication: Devices are verified using public key cryptography or password-based methods, ensuring only authorized entities gain access.
- Encryption: All data transmitted between the client and server is encrypted, preventing interception by malicious actors.
- Command Execution: Once authenticated, users can execute commands on remote devices, manage configurations, and monitor device performance seamlessly.
Why SSH is Crucial for IoT
As IoT ecosystems continue to expand, the significance of secure communication protocols like SSH becomes increasingly apparent. With billions of connected devices exchanging sensitive data, ensuring data integrity and confidentiality is a top priority for organizations and individuals.
Why SSH is Essential for IoT Environments
SSH offers several advantages that make it an ideal choice for securing IoT systems:
- Encryption: SSH encrypts all data transmissions, protecting against eavesdropping and data tampering.
- Authentication: Devices and users are authenticated using advanced cryptographic methods, reducing the risk of unauthorized access.
- Remote Management: SSH empowers administrators to manage IoT devices remotely, enhancing operational efficiency and reducing costs.
Key Features of IoT SSH Servers
IoT SSH servers come equipped with a variety of features designed to enhance security, efficiency, and usability. Some of the standout features include:
Read also:Mastering Dorm Room Cooking Healthy And Delicious Meals For College Students
1. Encrypted Data Transmission
All data exchanged between IoT devices and the SSH server is encrypted using cutting-edge cryptographic algorithms, ensuring that sensitive information remains secure during transit.
2. Multi-Factor Authentication
Modern IoT SSH servers support multi-factor authentication (MFA), adding an additional layer of security by requiring users to provide extra verification beyond just a password.
3. Scalability
IoT SSH servers are engineered to handle large-scale deployments, supporting thousands of connected devices without compromising performance or security.
Advantages of Using IoT SSH Servers
Implementing IoT SSH servers provides numerous benefits for both organizations and individuals. Some of the key advantages include:
Enhanced Security
By encrypting data transmissions and authenticating devices, IoT SSH servers significantly reduce the risk of cyberattacks and data breaches, ensuring your IoT infrastructure remains protected.
Improved Efficiency
Remote management capabilities allow administrators to monitor and control IoT devices from a centralized location, saving valuable time and resources while streamlining operations.
Cost Savings
Minimizing downtime and optimizing operations lead to substantial cost savings, making IoT SSH servers a cost-effective solution for managing IoT ecosystems.
How to Set Up an IoT SSH Server
Setting up an IoT SSH server involves several steps, from selecting the appropriate hardware and software to configuring security settings. Below is a step-by-step guide to help you get started:
Step 1: Choose the Right Hardware
Select a server that aligns with the performance and scalability requirements of your IoT deployment. Consider factors such as processing power, memory, and storage capacity to ensure optimal performance.
Step 2: Install SSH Software
Install an SSH server software package on your chosen hardware. Popular options include OpenSSH and Dropbear, both of which offer robust security features and user-friendly interfaces.
Step 3: Configure Security Settings
Set up strong passwords, enable public key authentication, and configure firewall rules to safeguard your IoT SSH server from unauthorized access and potential threats.
Security Best Practices for IoT SSH Servers
While IoT SSH servers provide a secure foundation for IoT communications, following best practices is essential for maximizing security. Below are some recommended strategies:
1. Use Strong Passwords
Create complex passwords that incorporate uppercase and lowercase letters, numbers, and special characters to deter brute-force attacks and enhance security.
2. Enable Public Key Authentication
Public key authentication offers a more secure alternative to password-based authentication, reducing the likelihood of unauthorized access and enhancing overall security.
3. Regularly Update Software
Keep your SSH server software up to date with the latest security patches and updates to protect against emerging threats and vulnerabilities.
Common Issues and Solutions
Despite their robust security features, IoT SSH servers may encounter issues that could impact performance or security. Below are some common challenges and their solutions:
1. Connection Failures
Solution: Review network configurations, ensure proper firewall settings, and verify that the SSH service is running on the server to resolve connection issues.
2. Authentication Errors
Solution: Carefully check username and password credentials and ensure that public key authentication is correctly configured to address authentication problems.
Real-World Case Studies
Several organizations have successfully implemented IoT SSH servers to enhance security and efficiency in their IoT deployments. Below are two real-world examples:
Case Study 1: Smart City Infrastructure
A major city implemented IoT SSH servers to manage its smart lighting and traffic management systems. The secure communication enabled by SSH helped reduce downtime, improve overall system performance, and ensure public safety.
Case Study 2: Industrial IoT
A manufacturing company deployed IoT SSH servers to monitor and control its production line equipment. The secure remote access capabilities allowed engineers to troubleshoot issues promptly, minimizing production disruptions and enhancing operational efficiency.
Emerging Trends in IoT SSH Technology
The future of IoT SSH technology is promising, with several emerging trends set to shape the landscape:
1. Quantum-Resistant Cryptography
As quantum computing becomes more prevalent, researchers are developing quantum-resistant cryptographic algorithms to ensure the long-term security of IoT SSH communications and protect against future threats.
2. AI-Powered Security
Artificial intelligence (AI) and machine learning (ML) technologies are being integrated into IoT SSH servers to enhance threat detection, response capabilities, and overall security, paving the way for smarter and more resilient IoT ecosystems.
Conclusion and Next Steps
In conclusion, IoT SSH servers are a powerful tool for securing IoT communications and managing connected devices. By understanding their functionality, advantages, and best practices, organizations and individuals can harness their full potential to build secure and efficient IoT ecosystems.
We encourage you to take action by implementing the strategies outlined in this guide and sharing your experiences with the community. Your feedback and insights can help others make informed decisions about IoT SSH server deployments. Don’t hesitate to explore our additional resources for more in-depth information on IoT security and technology.