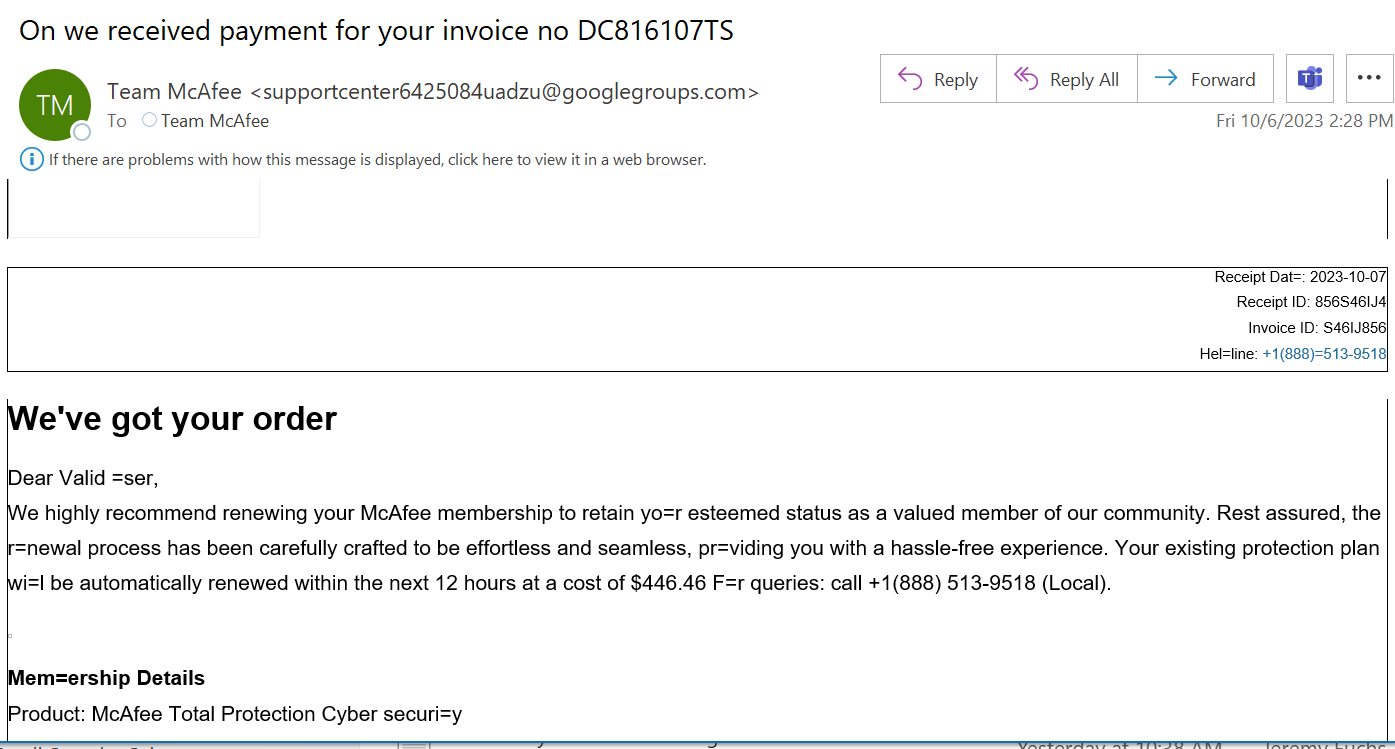
In today's digital age, McAfee spoofing has become a significant concern for individuals and businesses alike. Cybercriminals are using sophisticated techniques to deceive unsuspecting users, leading to potential security breaches and identity theft. Understanding the nature of McAfee spoofing is crucial to protect your personal information and maintain online safety.
As we increasingly rely on technology for communication, finance, and entertainment, the risks associated with cyber threats continue to grow. McAfee spoofing is one of the most prevalent tactics used by hackers to exploit vulnerabilities in digital systems. By impersonating legitimate entities, cybercriminals can gain unauthorized access to sensitive data, leading to devastating consequences.
This article aims to provide a detailed overview of McAfee spoofing, its implications, and effective strategies to safeguard against such attacks. Whether you're an individual user or a business owner, this guide will equip you with the knowledge and tools necessary to protect your digital presence.
Read also:Does Taron Egerton Have A Daughter Exploring The Life And Family Of The Renowned Actor
Table of Contents
- What is McAfee Spoofing?
- Types of Spoofing Attacks
- McAfee's Role in Cybersecurity
- The History of Spoofing
- Impact of McAfee Spoofing on Users
- Effective Prevention Tactics
- Tools and Resources for Protection
- Legal and Regulatory Aspects
- Real-World Examples of McAfee Spoofing
- Future Trends in Cybersecurity
What is McAfee Spoofing?
Spoofing, in the context of cybersecurity, refers to the act of disguising communication from an unknown source as being from a known, trusted source. McAfee spoofing specifically involves impersonating McAfee antivirus software or services to deceive users. This can take various forms, including fake emails, phishing websites, and malicious software designed to mimic legitimate McAfee products.
McAfee spoofing is particularly dangerous because McAfee is a well-known and trusted brand in the cybersecurity industry. Users are more likely to trust communications or software that appear to be from McAfee, making them vulnerable to attacks. Cybercriminals exploit this trust to gain access to personal information, financial data, and other sensitive details.
How Does McAfee Spoofing Work?
McAfee spoofing typically involves the following steps:
- Email Spoofing: Hackers send emails that appear to be from McAfee, often containing links to malicious websites or attachments that install malware on the user's device.
- Website Spoofing: Fake websites are created to resemble official McAfee pages, tricking users into entering their login credentials or downloading malicious software.
- IP Spoofing: Attackers falsify the IP address of their device to make it appear as if they are communicating from a legitimate McAfee server.
Types of Spoofing Attacks
Spoofing attacks come in various forms, each targeting different aspects of digital communication. Below are some of the most common types of spoofing:
1. Email Spoofing
Email spoofing involves sending emails with forged sender addresses to make them appear as if they are from a trusted source. This tactic is often used in phishing attacks to trick users into revealing sensitive information.
2. Website Spoofing
Website spoofing involves creating fake websites that mimic legitimate ones. These sites are designed to deceive users into entering their personal information or downloading malicious software.
Read also:Holly Rowe Wife A Comprehensive Look Into Her Life Career And Family
3. IP Spoofing
IP spoofing involves falsifying the IP address of a device to hide the attacker's identity or impersonate another device. This technique is commonly used in distributed denial-of-service (DDoS) attacks.
McAfee's Role in Cybersecurity
McAfee, founded in 1987 by John McAfee, has been a pioneer in the field of cybersecurity. The company is renowned for developing antivirus software that protects users from various digital threats. Over the years, McAfee has expanded its product offerings to include comprehensive security solutions for both individual users and businesses.
McAfee Biodata
| Full Name | John McAfee |
|---|---|
| Birth Date | September 3, 1945 |
| Place of Birth | Westminster, London, England |
| Education | Bachelor's degree in Mathematics from Roanoke College |
| Known For | Founder of McAfee Associates, a leading cybersecurity company |
The History of Spoofing
Spoofing has been a part of cybersecurity threats since the early days of the internet. As technology has evolved, so too have the methods used by cybercriminals to exploit vulnerabilities. The first recorded instances of email spoofing date back to the 1990s, coinciding with the rise of email as a primary means of communication.
Over the years, spoofing techniques have become increasingly sophisticated, with attackers using advanced algorithms and machine learning to create convincing impersonations. Despite efforts by cybersecurity experts to combat spoofing, it remains a significant threat to digital security.
Impact of McAfee Spoofing on Users
McAfee spoofing can have severe consequences for individuals and businesses. For individuals, the risks include identity theft, financial loss, and reputational damage. Businesses, on the other hand, face the potential for data breaches, regulatory fines, and loss of customer trust.
According to a report by the Federal Trade Commission (FTC), phishing attacks, including McAfee spoofing, resulted in over $54 million in losses in 2020 alone. This highlights the importance of staying vigilant and implementing robust security measures to protect against such threats.
Effective Prevention Tactics
Preventing McAfee spoofing requires a combination of technical solutions and user awareness. Below are some effective strategies to safeguard against spoofing attacks:
- Use Multi-Factor Authentication: Enable multi-factor authentication (MFA) for all accounts to add an extra layer of security.
- Verify Email Senders: Always verify the sender's email address before clicking on links or downloading attachments.
- Install Antivirus Software: Use reputable antivirus software, such as McAfee, to protect your device from malware and other threats.
- Stay Informed: Stay updated on the latest cybersecurity trends and threats to remain aware of potential risks.
Tools and Resources for Protection
Several tools and resources are available to help users protect against McAfee spoofing and other cyber threats. Some of the most effective options include:
- McAfee Total Protection: A comprehensive security suite that offers protection against malware, phishing, and other online threats.
- Phishing Filter Extensions: Browser extensions designed to detect and block phishing websites.
- Cybersecurity Training Programs: Online courses and workshops that educate users on best practices for staying safe online.
Legal and Regulatory Aspects
Cybersecurity is governed by various laws and regulations aimed at protecting users from digital threats. The General Data Protection Regulation (GDPR) in the European Union and the California Consumer Privacy Act (CCPA) in the United States are examples of legislation designed to safeguard personal data.
Organizations that fail to comply with these regulations may face significant fines and legal consequences. It is essential for businesses to implement robust security measures and adhere to legal requirements to protect their customers' information.
Real-World Examples of McAfee Spoofing
Several high-profile cases of McAfee spoofing have made headlines in recent years. One notable example involved a phishing campaign targeting McAfee users in 2019. The attackers sent emails claiming to be from McAfee, urging recipients to update their antivirus software. Those who followed the instructions were directed to a fake website where their login credentials were stolen.
Another case involved a fake McAfee support scam, where users were tricked into paying for unnecessary software updates. These incidents highlight the need for increased awareness and vigilance in detecting and preventing spoofing attacks.
Future Trends in Cybersecurity
As technology continues to evolve, so too will the methods used by cybercriminals to exploit vulnerabilities. Future trends in cybersecurity are likely to focus on artificial intelligence (AI) and machine learning (ML) to detect and prevent spoofing attacks.
Additionally, the rise of quantum computing may lead to new encryption techniques that offer greater protection against digital threats. Staying informed about these advancements is crucial for individuals and businesses to maintain their digital security.
Conclusion
In conclusion, McAfee spoofing poses a significant threat to digital security, with far-reaching implications for individuals and businesses. By understanding the nature of spoofing attacks and implementing effective prevention strategies, users can protect their personal information and maintain online safety.
We encourage readers to take action by enabling multi-factor authentication, verifying email senders, and staying informed about the latest cybersecurity trends. Additionally, consider sharing this article with others to help raise awareness about the dangers of McAfee spoofing and the importance of digital security. Together, we can create a safer online environment for everyone.