SSH remote IoT device tutorial is essential for anyone looking to secure their Internet of Things (IoT) devices. As more devices connect to the internet, ensuring secure communication becomes crucial. This guide will walk you through everything you need to know about setting up SSH for IoT devices.
With the rapid growth of IoT technology, the demand for secure communication methods has increased exponentially. Devices that were once standalone now require secure connections to transmit sensitive data. This tutorial will provide you with step-by-step instructions to set up SSH on your IoT devices.
Whether you're a beginner or an experienced developer, this guide will help you understand the importance of SSH and how it can protect your IoT devices from unauthorized access. By the end of this article, you'll be equipped with the knowledge to implement SSH securely and effectively.
Read also:Unveiling The Power Of Generation Alpha The Future Is Now
Table of Contents
- Introduction to SSH Remote IoT Device Tutorial
- What is SSH?
- Why Use SSH for IoT Devices?
- Setting Up SSH on IoT Devices
- Configuring SSH for IoT Devices
- Securing Your SSH Connection
- Best Practices for SSH in IoT
- Troubleshooting Common Issues
- Use Cases for SSH in IoT
- Conclusion
Introduction to SSH Remote IoT Device Tutorial
In today's interconnected world, IoT devices play a significant role in various industries, from smart homes to industrial automation. However, securing these devices is paramount to prevent unauthorized access and data breaches. SSH remote IoT device tutorial provides a detailed guide on how to establish secure communication between your IoT devices and remote servers.
This tutorial is designed for individuals and organizations that want to enhance the security of their IoT infrastructure. By the end of this guide, you'll have a clear understanding of SSH and its role in IoT security. Additionally, you'll learn practical steps to implement SSH on your devices.
SSH offers a secure way to access and manage IoT devices remotely. It encrypts data in transit, ensuring that sensitive information remains protected from potential threats. This tutorial will cover everything from the basics of SSH to advanced configuration options.
What is SSH?
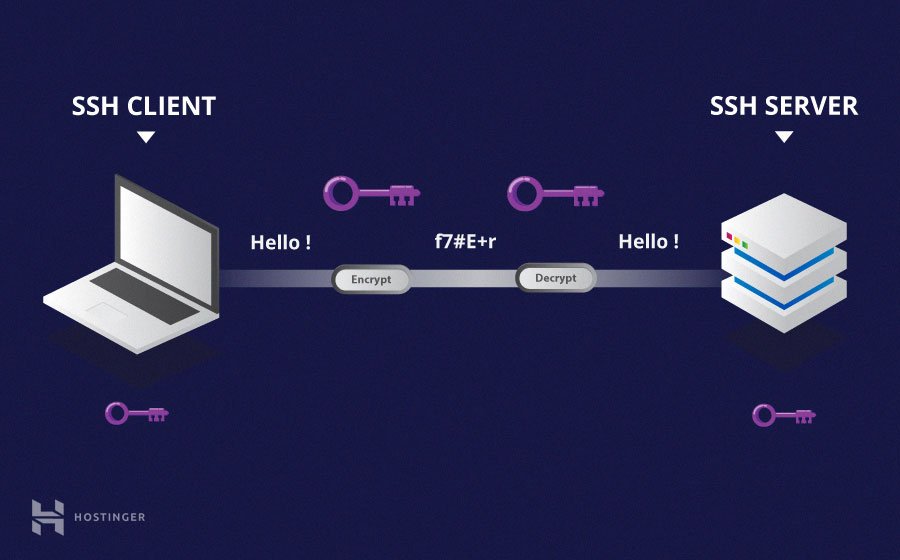
SSH, or Secure Shell, is a cryptographic network protocol used for secure communication over unsecured networks. It provides a secure channel for remote access, file transfer, and command execution. SSH ensures that data transmitted between devices is encrypted and protected from eavesdropping and tampering.
SSH operates on a client-server model, where the client initiates a connection to the server. Once the connection is established, users can securely manage their devices or transfer files. SSH is widely used in IoT environments due to its robust security features and ease of use.
Why Use SSH for IoT Devices?
Using SSH for IoT devices offers several advantages, including:
Read also:Trace Gallagher Married A Comprehensive Look Into The Personal Life Of The Renowned Journalist
- Encryption: SSH encrypts all data transmitted between devices, ensuring confidentiality.
- Authentication: SSH supports various authentication methods, such as password and public key authentication, to verify user identity.
- Integrity: SSH ensures data integrity by detecting any tampering during transmission.
- Compatibility: SSH is compatible with a wide range of IoT devices and operating systems.
With the increasing number of cyber threats targeting IoT devices, SSH provides a reliable solution for securing communication. By implementing SSH, you can protect your devices from unauthorized access and data breaches.
Setting Up SSH on IoT Devices
Preparation
Before setting up SSH on your IoT devices, ensure that you have the following:
- An IoT device with an operating system that supports SSH (e.g., Linux-based systems).
- A computer or laptop with SSH client software installed (e.g., PuTTY for Windows or Terminal for macOS/Linux).
- Basic knowledge of command-line interfaces and networking.
Installation
To install SSH on your IoT device, follow these steps:
- Connect to your IoT device via a terminal or command-line interface.
- Update your package manager to ensure you have the latest software versions.
- Install the SSH server by running the appropriate command for your operating system. For example, on Debian-based systems, use the following command:
sudo apt-get install openssh-server
Configuring SSH for IoT Devices
Once SSH is installed, you can configure it to suit your needs. The main configuration file for SSH is located at /etc/ssh/sshd_config. To edit this file, use a text editor such as nano or vi:
sudo nano /etc/ssh/sshd_config
Some important configuration options include:
- Port: Change the default SSH port (22) to a custom port for added security.
- PermitRootLogin: Disable root login to prevent unauthorized access.
- PasswordAuthentication: Disable password authentication and use public key authentication instead.
After making changes to the configuration file, restart the SSH service to apply the new settings:
sudo systemctl restart ssh
Securing Your SSH Connection
Securing your SSH connection is crucial to protect your IoT devices from potential threats. Here are some tips to enhance the security of your SSH setup:
- Use Strong Passwords: If you must use password authentication, ensure that your passwords are strong and unique.
- Enable Two-Factor Authentication: Add an extra layer of security by enabling two-factor authentication for SSH.
- Limit Access: Restrict SSH access to specific IP addresses or networks using firewall rules.
By implementing these security measures, you can significantly reduce the risk of unauthorized access to your IoT devices.
Best Practices for SSH in IoT
To ensure optimal performance and security, follow these best practices when using SSH for IoT devices:
- Regular Updates: Keep your SSH server and client software up to date with the latest security patches.
- Backup Configuration Files: Regularly back up your SSH configuration files to prevent data loss.
- Monitor Logs: Review SSH logs regularly to detect any suspicious activity.
Adhering to these best practices will help you maintain a secure and reliable SSH setup for your IoT devices.
Troubleshooting Common Issues
While setting up SSH for IoT devices, you may encounter some common issues. Here are some solutions to help you troubleshoot:
- Connection Refused: Ensure that the SSH service is running and the correct port is open.
- Authentication Failed: Verify that your username and password are correct or check your public key configuration.
- Slow Connection: Optimize your network settings and ensure that your device has sufficient resources.
Refer to the official SSH documentation for more detailed troubleshooting tips.
Use Cases for SSH in IoT
SSH has numerous applications in IoT environments, including:
- Remote Device Management: Use SSH to manage IoT devices remotely, such as updating firmware or configuring settings.
- Secure Data Transfer: Transfer files securely between IoT devices and servers using SSH.
- Network Monitoring: Monitor network traffic and device performance using SSH-based tools.
These use cases demonstrate the versatility and importance of SSH in IoT applications.
Conclusion
This SSH remote IoT device tutorial has provided you with a comprehensive guide to setting up and securing SSH for your IoT devices. By following the steps outlined in this article, you can ensure that your devices are protected from unauthorized access and data breaches.
Remember to regularly update your SSH software and follow best practices to maintain a secure and reliable setup. We encourage you to share this article with others and leave a comment below if you have any questions or suggestions. Additionally, explore our other articles for more tips on IoT security and technology.